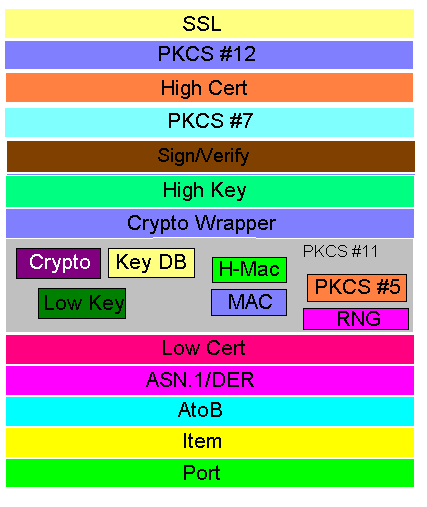
decal's security shed
data encryption
internal
Algorithmic Information
List of encryption algorithms generated by: openssl ciphers -v ALL
external
Crypto References
Attacks & Cryptanalysis
Statement of Federal Service for Early Cryptanalysis
Password Interception in a SSL/TLS Channel
Brice Canvel, Alain Hiltgen, Serge Vaudenay, Martin Vuagnoux
Advances in Cryptology -- CRYPT'03, Lecture Notes in Computer Science, No.2729, pp. 583-599, Springer-Verlag, 2003.
Subtly malicious crypto code contest
heartbleed.com
rc4nomore.com
breachattack.com
drownattack.com
poodle.io
weakdh.org
freakattack.com
ccsinjection.lepidum.co.jp
mitls.org/pages/attacks/SMACK
bettercrypto.org
badssl.com
Cipher security summary @ Wikipedia
Hash function security summary @ Wikipedia
Guidelines & Standards
SSL and TLS Deployment Best Practices
TLS Attacks via: mitls.org
Wikipedia Cryptography Portal
Outline of cryptography @ Wikipedia
Cryptography
HTTP/2 TLS v1.2 Cipher Suite Blacklist
The TLS Protocol Version 1.2
TLS Working Group of the IETF Discussion Archive
NIST's Cryptographic Algorithm Validation Program (CAVP)
Preview of the Online Cryptography Course
Virginia Tech Certification Authority: Encryption Glossary
FIPS-PUB: Federal Information Processing Standards Publications
X.509 Style Guide
PKCS#11 Cryptographic Token Interface Current Mechanisms Specification
PKCS#7: Cryptographic Message Syntax (CMS)
AES Security
Access Control for Electronic Services SSL Application Form for Notarization
Canadian Accounting Trust Services for Information Technology
Standards for Efficient Cryptography Group
certificate-transparency.org
A verified reference TLS implementation
Basic Cryptanalysis
Cypherpunks Distributed Data-heaven
Crypto Law Survey: existing and proposed cryptography laws by country
Crypto Links
How to use Forum Sentry for SAML SSO
Parsing X.509 Certificates with OpenSSL and C
Academic Whitepapers
APA, MLA and Chicago Style Citation Guides
Cryptographic Hash Function Basics
How to Protect DES Against Exhaustive Key Search (An Analysis of DESX)*
Kilian & Rogaway (
2000)Efficient Permutation Instructions for Fast Software Cryptography
Lee, et al. (
2001)Peter Gutmann - Security system researcher at the University of Auckland
Herbert Haas Security Page including RSA, DH, and ECC Materials
Multidigit Multiplication for Mathematicians by DJB
The Monkeysphere Project: Use OpenPGP with TLS
RFC2240: OpenPGP Message Format
RFC2712: Addition of Kerberos Cipher Suites to Transport Layer Security (TLS)
RFC3447: RSA Cryptography Specifications Version 2.1
RFC4270: Attacks on Cryptographic Hashes in Internet Protocols
RFC5081: Using OpenPGP Keys for Transport Layer Security (TLS) Authentication
Hash Functions in Cryptography
Vendor Documentation
SSL/TLS in Detail
IXpsSignatureManager interfaceA Simple Guide to Cryptography ( ©Wrux Press 1998 )
MSDN Dev Center -
CryptographyKerberos for the Busy Admin
Mozilla Pending CA Certificate List
UNIX
crypt() using SHA-256 and SHA-512.Photoris: Session-Key Management Protocol
Blogs & Articles
Secure Sockets Layer @ InspIRCd Wiki
Why We Need to Move to SHA-2
Bibliography of the International Cryptology Conference (CRYPTO)
Privacy Rights Fact Sheets
CryptoLounge Wiki - Category: Algorithm (on the WayBack Machine
Cryptographic Attacks @ Wikipedia
Broken Cryptography Algorithms @ Wikipedia
Cryptographic Protocols @ Wikipedia
MD5 and Perspectives
EKE: Encapsulated Key Escrow with Related Work & Links
How can I audit which type of Block Mode encryption is being used when no source code is available?
Defeating AES Without a PhD (Burp Suite Decoder Tool)
FAQ on the attacks against AES-128, AES-192 and AES-256 (by the University of Luxembourg)
SSH/SSL Private Key Formatting in Microsoft's .NET Framework
bletchley: A collection of practical cryptanalysis tools
Cryptographic Key Length Recommendation
GnuPG Cheat Sheet
Public Key Cryptography Standards (PKCS)
Military Cryptanalysis
CAcert: FREE digital certificates for everyone
On Applying Molecular Computation to the Data Encryption Standard
Nucleic Acid DataBase
What is DNA Computing? by RSA® Laboratories
Passwords^12 Media Archive
The quest for the most diminutive munitions program
Codesigning Introspection Commands
Speaking of Security: The RSA Blog & Podcast
: Distributed systems programer and cryptanalyst
ASN.1 Made Simple -- What is ASN.1?
learncryptography.com
Diffie-Hellman Explained
An Overview of Cryptography by Gary C. Kessler
Tools
certificate.revocationcheck.com
certificate.fyicenter.com
certificatedetails.com
howsmyssl.com
casecurity.org
OpenSSL: Manually verify a certificate against an OCSP
JavaScript Implementations of Many Crypto Algorithms
Stand-alone & Web-based SSL Certificate Tools
ASN.1 Playground - learn, play, test
An Introduction to XML Signature and XML Encryption with XMLSec
Bloop ˙ theoretic infosec technique to share disposable messages
paste.sh ˙ encrypted pastebin
the matasano crypto challenges ˙ (learn core cryptographic principles through problem solving)
community-driven global initiative which grew out of the first comprehensive public audit and cryptanalysis of the widely used encryption software TrueCrypt&circler;
Online WPA cracker with stats
Distributed WPA PSK auditor
crackstation.net
onlinehashcrack.com
CISSP Cryptography Domain Flash Cards
Software & Hardware Vendors
Cryptera ˙ POS hardware vendor
WhisperSystems ˙ open source security for mobile devices
RSA (Rivest, Shamir & Adleman) ˙ The Security Division of EMC2
Crypto-Sign® - From Transaction Security, Inc.
Botan: Crypto and TLS for C++11
GPG Tools
The Legion of the Bouncy Castle
The Zfone™ Project
OpenPGP.js
encrypt.to
Non-Profit Organizations and Such..
openca.org
letsencrypt.org
istlsfastyet.com
zodiologists.com
Hash function security summary @ Wikipedia
Cipher security summary @ Wikipedia
Cryptocurrencies
Block chain entry on Bitcoin Wiki site
Vintage & Historical Reference
Electronic Cipher Machines according to the Maritime Park AssociationCipher Machines Timeline
History of cryptography @ Wikipedia
Cryptanalysis of ciphers published by a northern California serial killer in the late 1960's and early 1970's